
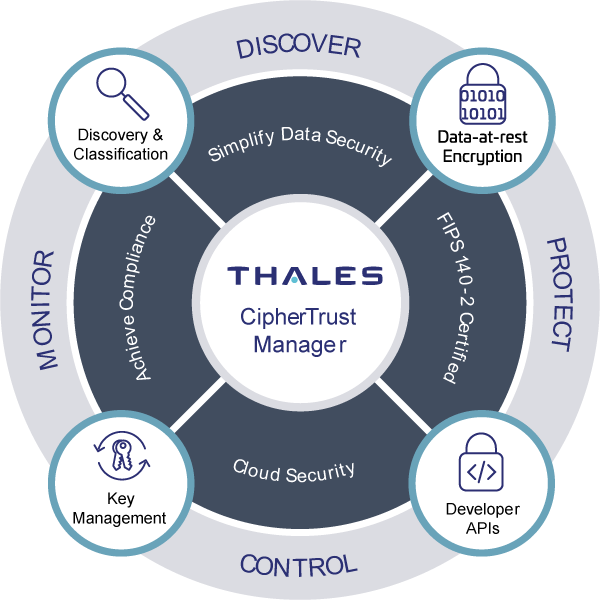
CipherTrust Data Security Platform
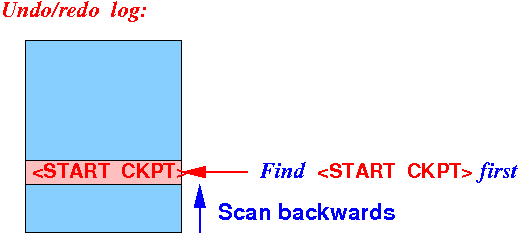
Recovering using an undo/redo log

Solved We are using undo/redo logging to recover the

Endpoint Privilege Management - Endpoint Protection
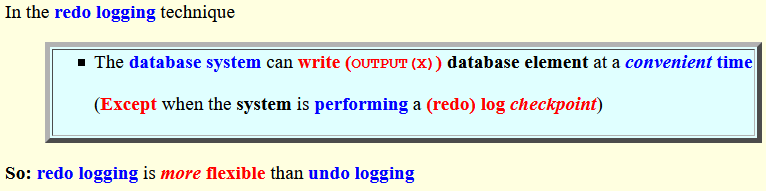
Intro to Undo/redo logging

/images/thumb/a/a8/Boot-Someone-Out

How to Protect Your Network from Cyber Attacks: A System
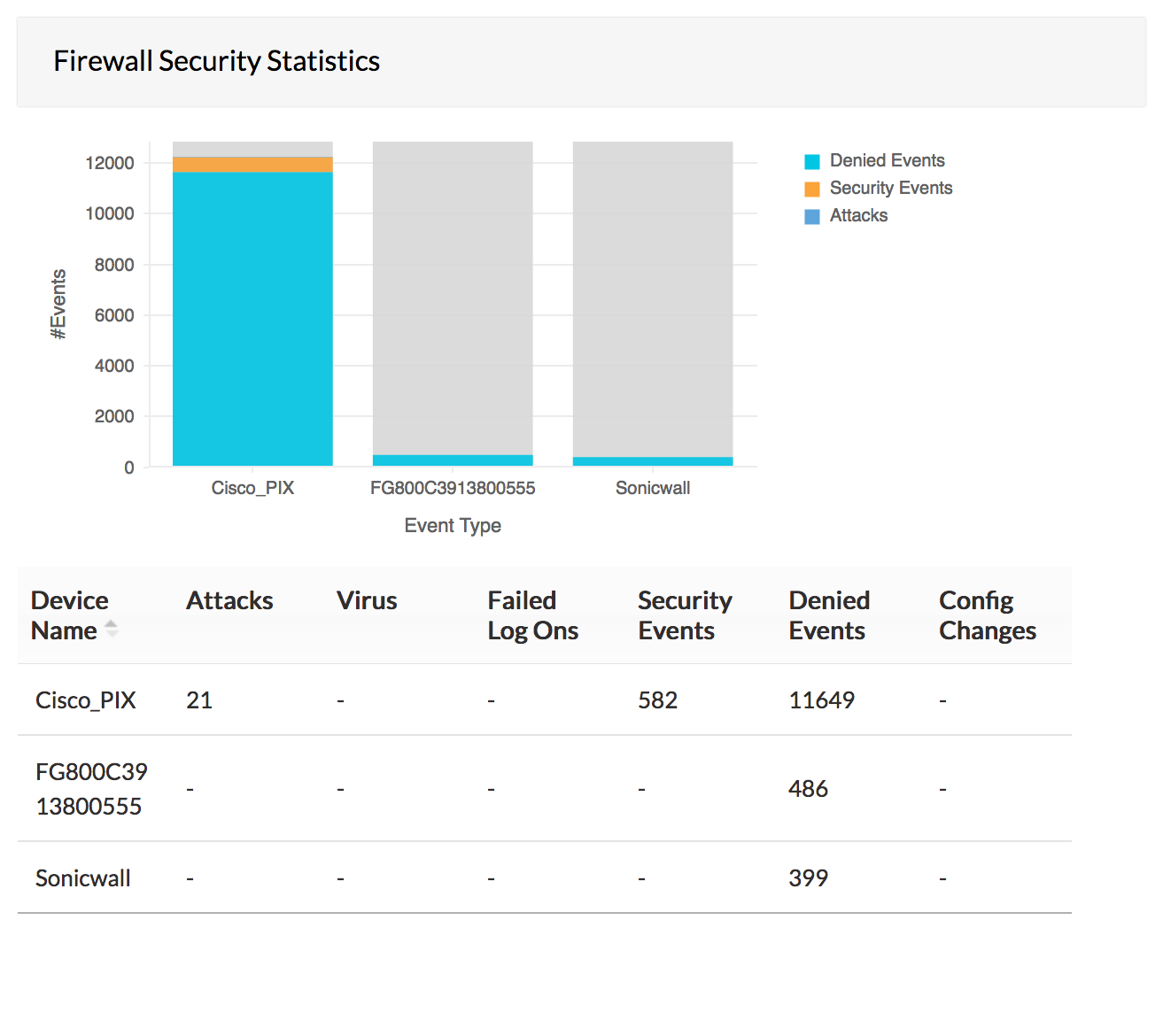
Firewall Analysis Tools Firewall Security Logs - ManageEngine Firewall Analyzer

To Help You Secure Your Email, Private Portal Is Now Available—For

Oracle dba interview questions with answer

How to Choose an EDR Solution for a Hacked Network

Imperva and Keysight: Defend Sensitive Applications and Data

Information, Free Full-Text

Understanding Syslog: Servers, Messages & Security
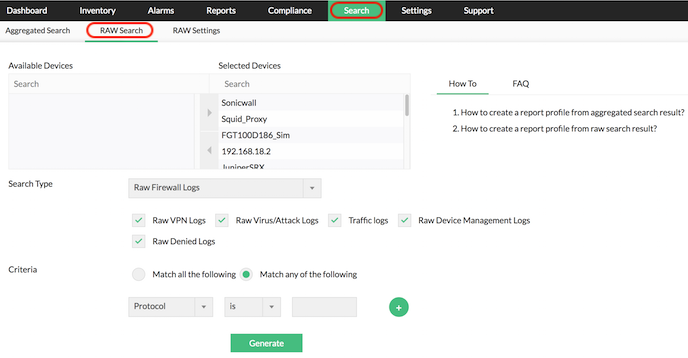
Firewall Forensics Tools Firewall Raw Log Search & Reports







