
Popular “smart” device follows commands issued by its own speaker. What could go wrong?

s Alexa reports 'Alexa versus Alexa', an attack method that hacks itself with voice commands - GIGAZINE

OWASP CODE REVIEW GUIDE - Bad Request

Best Home Security Systems That Work with Alexa in 2024

Best Home Security Systems That Work with Alexa in 2024
What is a Backdoor Attack, Shell & Trojan Removal

Hacking reality

Pentesting Network, HackTricks

A survey on security analysis of echo devices - ScienceDirect

Technical Advisory: Pulse Connect Secure – RCE via Uncontrolled Gzip Extraction (CVE-2020-8260), NCC Group Research Blog

What to Do When You've Been Hacked

Computer Systems Security: Planning for Success

The Mirai Confessions: Three Young Hackers Who Built a Web-Killing Monster Finally Tell Their Story
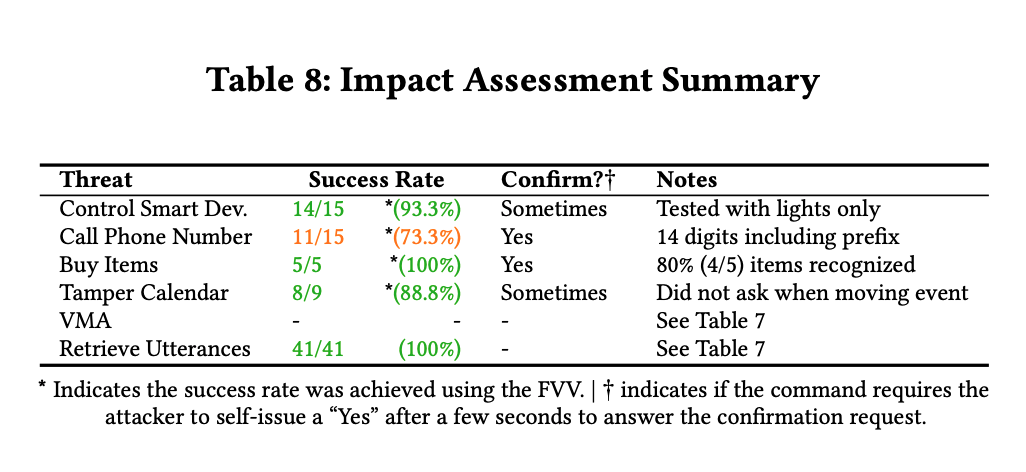
Attackers can force Echos to hack themselves with self-issued commands
GitHub - seeu-inspace/easyg: Here I gather all the resources about hacking that I find interesting






